Abstract: Networks usually consist of a wide range of devices from different vendors that require some means of authenticating users before they are granted access to resources. With that comes the added administrative burden of having to manage all the different accounts on each device; Remote Authentication Dial In User Service (RADIUS), is one means of countering this issue by providing a centralized infrastructure for authentication and accounting.
Now there are a lot of technical papers on configuring devices for RADIUS but I’m going to be doing things a little different in this article; I’m going to be giving you a brief overview of RADIUS, how it operates and how to incorporate it into any Cisco routers that you may have in your network.
Now there are a lot of technical papers on configuring devices for RADIUS but I’m going to be doing things a little different in this article; I’m going to be giving you a brief overview of RADIUS, how it operates and how to incorporate it into any Cisco routers that you may have in your network.
What is RADIUS?
RADIUS is a widely implemented networking protocol sometimes referred to as a client/server protocol, which provides a centralize mechanism of administering Users Account information. These can be usernames, passwords and privilege level for each account. AAA which stands for Authentication, Authorization and Accounting, are the core foundations upon which RADIUS is built. Authentication is the process by which the RADIUS server verifies the user requesting access before it is granted where as Authorization deals more with the level of access granted to a particular account. The Accounting aspect logs user’s session, thereby allowing an administrator to ascertain the length of time a specific account may be using the resource for and also to perform other administrative tasks.
Before a device can become a RADIUS client it first must be configured with the same pre-shared key as is configured on the RADIUS server thus allowing it to be able to pass user credentials onto the RADIUS server for verification.
When a user needs to access resources, they are required to provide credentials so as to verify that they have the required privileges to get that level of access to the given resource; this may be access to a Router, Switch, Access Point, Firewall or just data on a File Server.
These credentials are passed to a RADIUS client who then forwards it to the RADIUS server. The RADIUS server queries the credentials against its database before a result of access-accept or access-reject is sent back to the RADIUS client. Note for our example the RADIUS client will be a Cisco800 series router, specifically a Cisco 871; the database will be Active Directory configured and running on a Windows Server 2008 box; This article is focused on the configuration of the Cisco router.
Figure 1
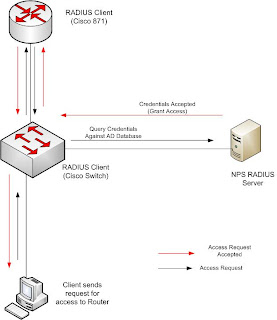
Showing the Authentication process when the user tries to access the router
Configure the Cisco 871
As a Cisco administrator you should already know the very basics at least of setting up your device but for those of you that have never configured one before, I’m going to go through these basic steps thus allowing even a novice to get any Cisco router configured to use RADIUS.
To connect to your Cisco Device you will need a terminal program such as HyperTerminal that comes with Windows XP or if you’re using Windows Vista like me then you’ll need a third party software; I like PUTTY so I’ll be using this throughout the lab.
1. First we need to configure the terminal software with the correct Serial settings as listed below after which we would begin the session by clicking open.
· Bits per sec : 9600
· Data bits : 8
· Parity : none
· Stop bits : 1
· Flow control : none
Figure 2
Configure the Cisco 871
As a Cisco administrator you should already know the very basics at least of setting up your device but for those of you that have never configured one before, I’m going to go through these basic steps thus allowing even a novice to get any Cisco router configured to use RADIUS.
To connect to your Cisco Device you will need a terminal program such as HyperTerminal that comes with Windows XP or if you’re using Windows Vista like me then you’ll need a third party software; I like PUTTY so I’ll be using this throughout the lab.
1. First we need to configure the terminal software with the correct Serial settings as listed below after which we would begin the session by clicking open.
· Bits per sec : 9600
· Data bits : 8
· Parity : none
· Stop bits : 1
· Flow control : none
Figure 2

2. After you have clicked open, you will be prompted to enter the credentials to gain access to the device. These credentials would be what you have configured before on the router or if it’s a brand new router you will have to use Cisco’s default credentials for that particular model. As was stated before the model of router I’m using is a Cisco 871 series and the default credentials for that are cisco, cisco for the username and password respectively.
3. Next we configure a host name with the following commands:
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname Cisco871
4. Depending on the role your router is going to play in your network your interfaces will be configured accordingly. For this example I already have a fully operational network therefore I only need to configure the WAN interface to receive an IP address and enable the telnet interface so that I can access the router from any pc or laptop as opposed to using the direct serial connection.
Cisco871(config)# interface fastethernet 4
Cisco871(config-if)#ip address dhcp
Cisco871(config-if)#noshutdown
5. Then we enable the AAA new-model, specify the RADIUS server and a group to be used.
Cisco871(config)#aaa new-model
Cisco871(config)#aaa authentication login CISCO group radius local
6. Specify which interface RADIUS will be accepting connections on.
Cisco871(config)#ip radius source-interface FastEthernet 4
7. Continuing along, we’re going to add the RADIUS server and the key noting that the key used would be the same key that was configured on the RADIUS server.
Cisco871(config)#radius-server host xxx.xxx.xxx.xxx
Cisco871(config)#radius-server key xxxx
8. Our last step is to configure the same RADIUS group (CISCO) we defined earlier under the vty lines as the authentication method to be used.
Cisco871(config)#line vty 0 4
Cisco871(config)# login authentication CISCO
Cisco871(config)#transport input telnet
At this stage we should be able to use telnet to connect to the router and provide the credentials of a user in our Active Directory database with the required “dial in” access.
Further reading on RADIUS can be done in article RFC 2865 of The Internet Engineering Task Force (IETF) website.
3. Next we configure a host name with the following commands:
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hostname Cisco871
4. Depending on the role your router is going to play in your network your interfaces will be configured accordingly. For this example I already have a fully operational network therefore I only need to configure the WAN interface to receive an IP address and enable the telnet interface so that I can access the router from any pc or laptop as opposed to using the direct serial connection.
Cisco871(config)# interface fastethernet 4
Cisco871(config-if)#ip address dhcp
Cisco871(config-if)#noshutdown
5. Then we enable the AAA new-model, specify the RADIUS server and a group to be used.
Cisco871(config)#aaa new-model
Cisco871(config)#aaa authentication login CISCO group radius local
6. Specify which interface RADIUS will be accepting connections on.
Cisco871(config)#ip radius source-interface FastEthernet 4
7. Continuing along, we’re going to add the RADIUS server and the key noting that the key used would be the same key that was configured on the RADIUS server.
Cisco871(config)#radius-server host xxx.xxx.xxx.xxx
Cisco871(config)#radius-server key xxxx
8. Our last step is to configure the same RADIUS group (CISCO) we defined earlier under the vty lines as the authentication method to be used.
Cisco871(config)#line vty 0 4
Cisco871(config)# login authentication CISCO
Cisco871(config)#transport input telnet
At this stage we should be able to use telnet to connect to the router and provide the credentials of a user in our Active Directory database with the required “dial in” access.
Further reading on RADIUS can be done in article RFC 2865 of The Internet Engineering Task Force (IETF) website.

No comments:
Post a Comment